Istio as the Strategic Successor to App Mesh
Istio is a CNCF‑graduated, open source service mesh built around Envoy that provides traffic management, security, and observability for microservices, and is widely adopted across cloud‑native environments. Because applications do not need to import Istio‑specific libraries or inherit framework classes, workloads remain decoupled from the mesh and can be moved or replatformed with minimal change if strategies evolve in the future
Istio now supports both sidecar and ambient (sidecarless) modes, allowing teams to modernize incrementally and run workloads across Kubernetes clusters, VMs, and heterogeneous infrastructure. This architectural flexibility makes it a natural successor for organizations moving away from App Mesh while preserving or improving their networking, resilience, and security posture
Where Saaras Fits: Istio, But FIPS‑Validated and FedRAMP‑Ready
Saaras provides a hardened, 100% upstream‑compatible Istio and Envoy distribution compiled against FIPS 140‑2 validated cryptographic modules, tested and verified. Because the distribution is pure upstream, existing Istio configurations and policies continue to work without changes, so moving from community Istio or another Envoy‑based mesh to Saaras typically takes days instead of weeks
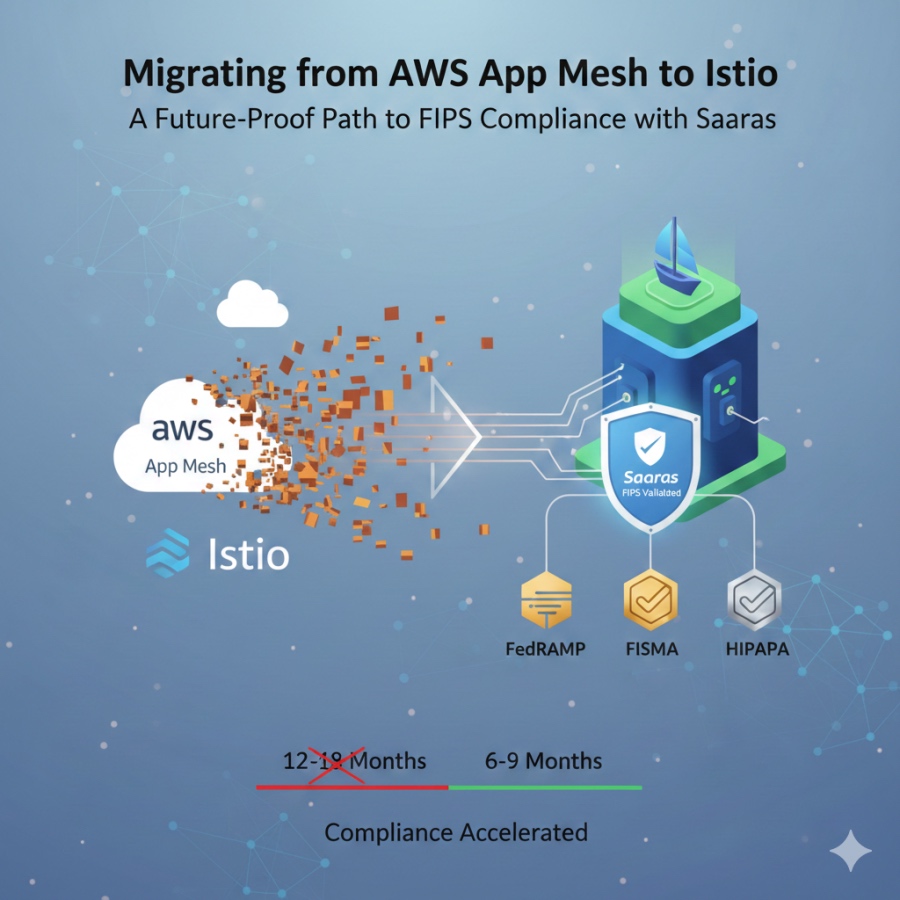
The Saaras Istio FIPS Subscription is designed for FedRAMP and other regulated environments, bundling FIPS‑validated crypto, validated security controls, and pre‑built compliance documentation to help teams cut their FedRAMP authorization timeline roughly from 12-18 months down to about 6-9 months. It targets frameworks such as FedRAMP, FISMA, HIPAA, PCI DSS, SOX, and DoD requirements, providing a cryptographic foundation that can be reused across multiple audits
Platform Scope: AWS, Gov Clouds, and Hybrid Topologies
For organizations currently on AWS App Mesh, Saaras’ distribution supports AWS GovCloud, Azure Government, Google Cloud, and on‑premises Kubernetes, including air‑gapped and restricted environments common in government and defense. This means teams can migrate from App Mesh on EKS to Istio while also planning for future multi‑cloud or hybrid deployments without re‑architecting their mesh posture
Because Istio also supports workloads on VMs, App Mesh users who still have services on EC2 can bring those workloads into the same mesh by deploying Envoy sidecars and registering them as first‑class citizens, with FIPS‑validated cryptography enforced consistently via Saaras
From App Mesh to Istio with Saaras: A Practical Flow
1. Deploy Saaras Istio FIPS alongside App Mesh
Install Saaras’ FIPS‑validated Istio, CRDs, and gateways into your EKS clusters while App Mesh continues to serve existing traffic
2. Enroll namespaces into the Saaras‑backed mesh
Label namespaces for sidecar injection (or ambient participation where applicable) so that new pod restarts begin to receive Istio sidecars or ambient data‑plane handling with FIPS‑validated Envoy binaries
3. Recreate App Mesh policies using Istio primitives
Translate App Mesh routing, retries, timeouts, and mTLS configurations into Istio VirtualServices, DestinationRules, AuthorizationPolicies, and PeerAuthentication, with Saaras ensuring those policies execute over FIPS‑validated crypto
4. Cut traffic over and decommission App Mesh
Gradually shift traffic to the Istio‑based mesh, validate observability and security behavior, then remove App Mesh resources once confidence is established
Throughout this process, Saaras provides 24/7 enterprise support, training, troubleshooting help, and compliance documentation, reducing both operational and governance overhead for platform teams
Why Saaras Is Attractive for Regulated App Mesh Users
For teams leaving App Mesh and heading toward stricter regulatory requirements, Saaras offers three key advantages.
- Compliance acceleration
FIPS 140‑2 Level 1 modules, validated controls, and pre‑built documentation shorten FedRAMP and related certification paths - Operational stability and lifecycle management
Support for the four most recent Istio versions, regular FIPS‑certified updates, and hardened builds provide predictable maintenance windows and long‑term stability - Enterprise‑grade ingress and observability
Full‑featured FIPS‑ready Envoy plus EnRoute API gateway give advanced routing, security, and observability at the edge, which one customer reference notes helped eliminate downtime and scale ingress cleanly
Conclusion
For organizations affected by the end of AWS App Mesh, moving to Istio is a natural way to regain control over the service mesh layer while avoiding future lock‑in. Saaras Istio FIPS Subscription extends that move with a hardened, FIPS 140‑2 validated distribution that is fully upstream‑compatible and tailored for FedRAMP and other regulated environments
By combining Istio’s open, flexible architecture with Saaras’ validated cryptography, compliance assets, and 24/7 expert support, platform and security teams can modernize their mesh, satisfy auditors, and reduce migration risk in a single, coherent step
Istio provides a vendor‑neutral, CNCF‑governed mesh that runs across Kubernetes, VMs, and multiple clouds, which reduces the long‑term risk of another deprecation impacting your architecture. Saaras then adds FIPS‑validated crypto and compliance support on top of Istio, which is particularly important for regulated workloads.
No. The Saaras Istio FIPS distribution is pure upstream Istio with no functional modifications, so existing Istio resources and policies work without changes and migration usually completes in days rather than weeks.
Saaras supports AWS GovCloud, Azure Government, Google Cloud, and on‑prem Kubernetes clusters, including air‑gapped and restricted environments used in government and defense. This lets you standardize on one FIPS‑validated mesh across multiple deployment models.
Saaras combines FIPS‑certified components with pre‑built compliance documentation and expert guidance, which can reduce a typical FedRAMP authorization timeline from about 12-18 months to roughly 6-9 months. This saves significant time for security, compliance, and platform teams during the authorization process.