Understanding FIPS and FedRAMP Observability Requirements
FedRAMP observability focuses on the continuous monitoring and assessment of cloud service providers' security posture, ensuring transparency and accountability in safeguarding federal data. This approach extends far beyond traditional monitoring, incorporating stringent security controls based on NIST SP 800-53 Rev. 5, particularly within the Audit and Accountability (AU), System and Communications Protection (SC), System and Information Integrity (SI), and Incident Response (IR) families.
The fundamental principle underlying FedRAMP observability is continuous monitoring with automated compliance validation. Federal agencies require real-time visibility into security-relevant events, comprehensive logging capabilities, and machine-readable evidence collection for audit purposes. This creates a paradigm shift from reactive monitoring to proactive security validation, where every system interaction must be tracked, validated, and documented according to federal standards.
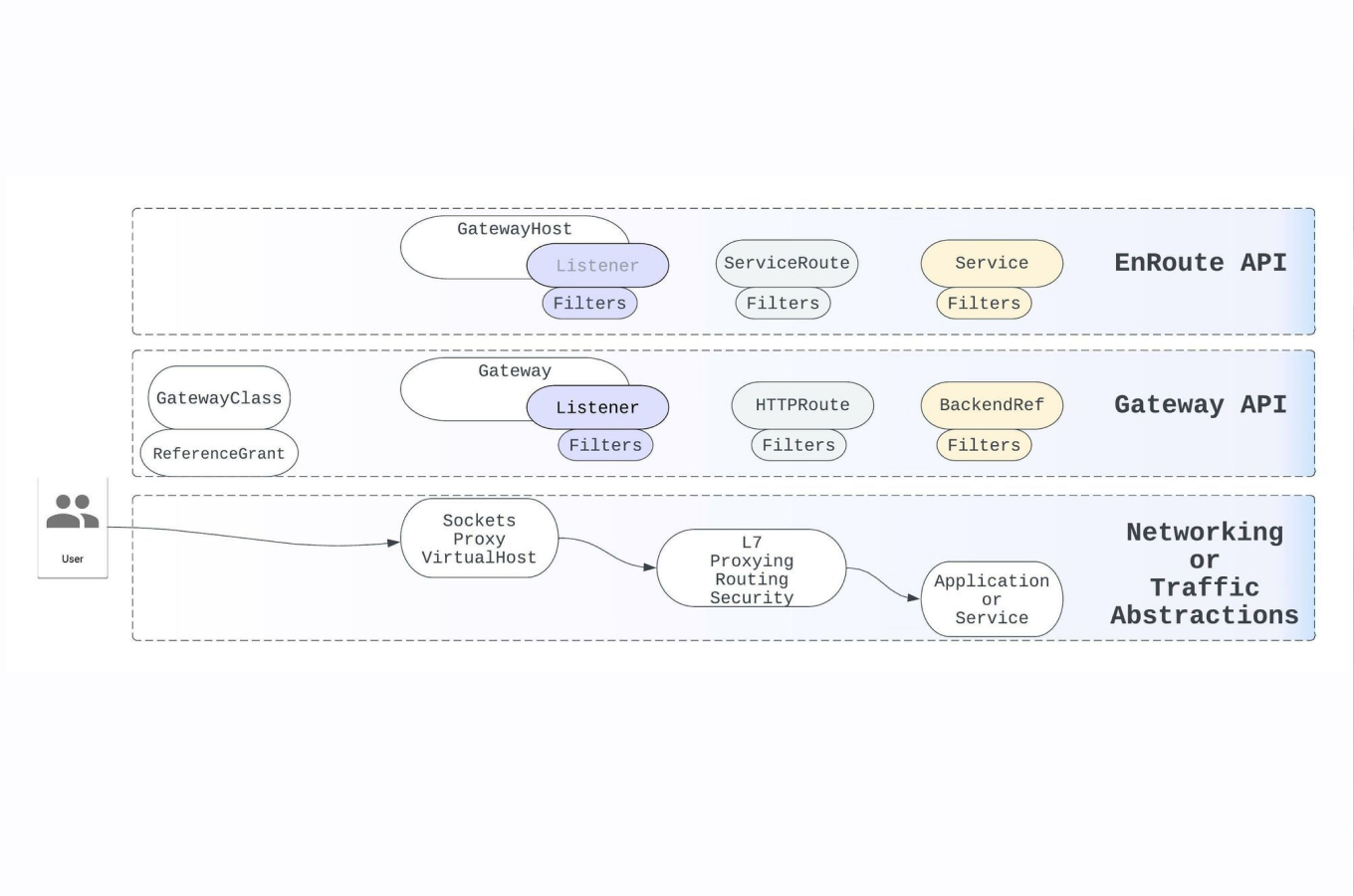
FIPS validation adds another layer of complexity, ensuring that cryptographic modules within observability solutions meet stringent security requirements for protecting sensitive data. This includes validation of encryption algorithms, key management processes, and secure communications protocols. Organizations implementing Zero Trust, FIPS, and FedRAMP frameworks must understand how these requirements integrate with cloud-native architectures and Kubernetes environments.
The IEEE analysis of FedRAMP authorization processes highlights the importance of standardized security controls and continuous monitoring capabilities. These requirements form the foundation for observability solutions that can meet federal compliance standards while maintaining operational efficiency.
Technical Differences from Standard Cloud Monitoring
FedRAMP observability requirements differ significantly from standard cloud monitoring approaches in several critical areas. While traditional monitoring focuses on predefined metrics and thresholds, FedRAMP-compliant observability extends this with comprehensive security logging, automated compliance reporting, and AI-powered incident response capabilities.
Standard cloud monitoring platforms like AWS CloudWatch, Azure Monitor, and Google Cloud Monitoring provide basic metrics, logs, and traces but often lack the depth of security features required by federal standards. FedRAMP-compliant solutions must implement continuous logging of security-relevant events, regular monitoring and auditing of logs, and automated validation of security controls using machine-readable evidence.
The technical architecture of FedRAMP observability platforms incorporates pre-validated controls, reusable security documentation, and audit-ready evidence collection. According to LogicMonitor's FedRAMP authorization analysis, these platforms can reduce authorization timelines by enabling agencies to reuse security packages and minimize custom reviews. Organizations implementing Zero Trust service mesh architectures benefit from integrated security validation and continuous compliance monitoring.
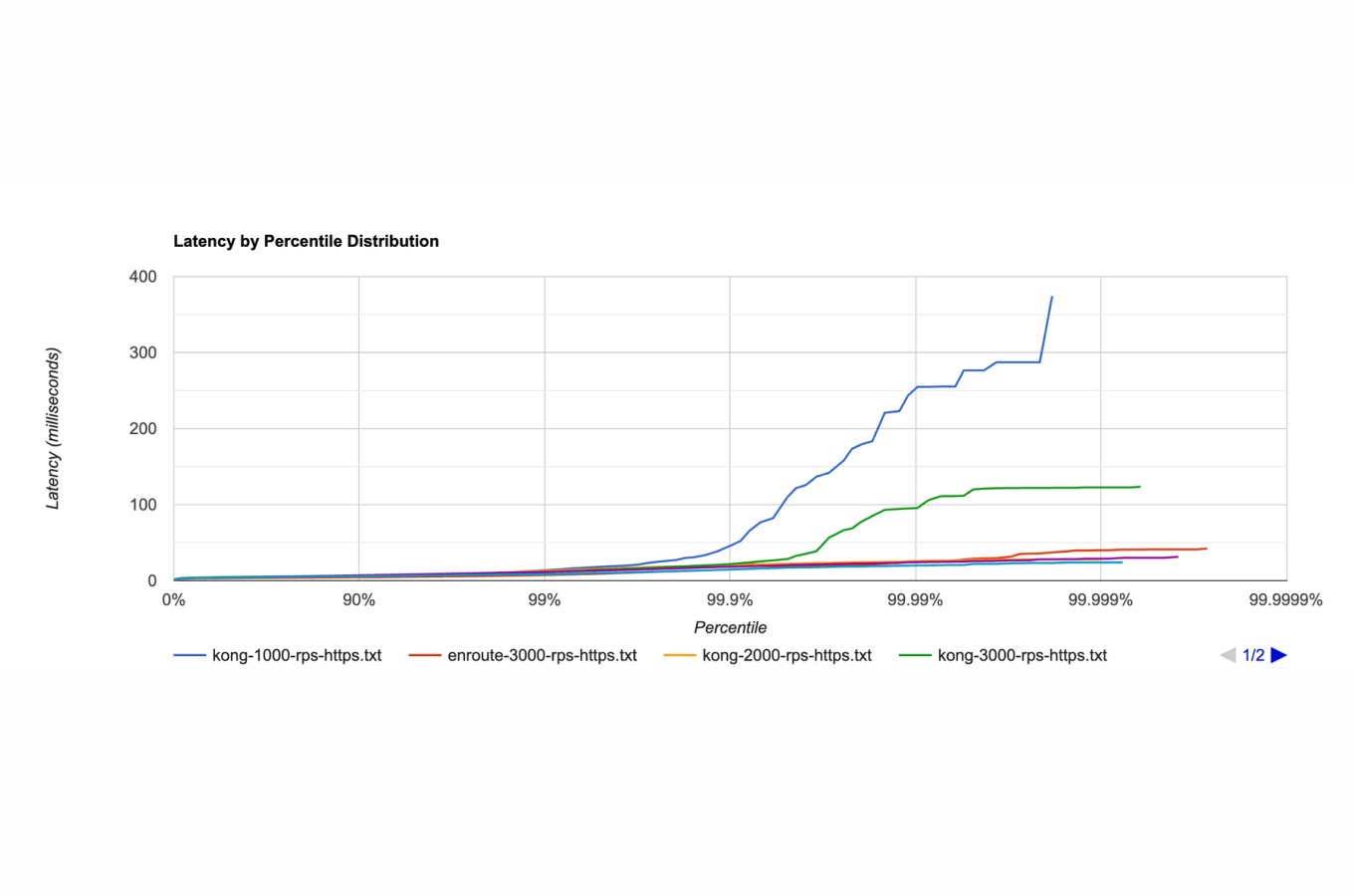
Performance optimization becomes critical when implementing FIPS-validated cryptographic modules. The New Relic study demonstrates that organizations can improve mean time to resolution (MTTR) by 80% using advanced observability tools, but FIPS compliance may introduce additional overhead that requires careful optimization and robust security policy implementation.
Implementation Strategies and Best Practices
Successful implementation of FIPS and FedRAMP observability requires a strategic approach that addresses both technical requirements and organizational capabilities. The foundation begins with establishing proper boundary definitions and security control mapping, as outlined in the FedRAMP boundary policy RFC.
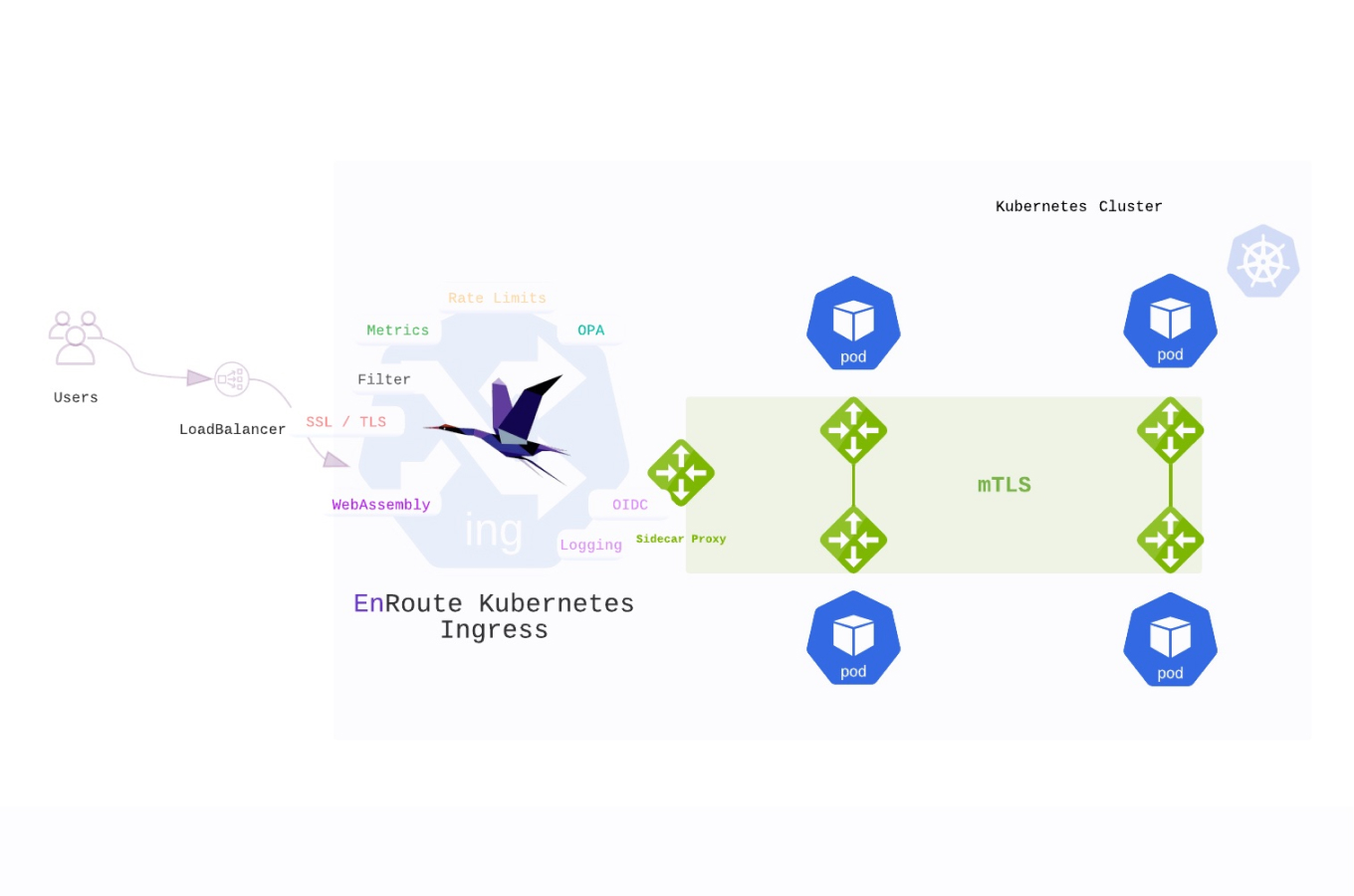
Organizations must implement end-to-end encryption and mutual TLS (mTLS) authentication throughout their observability stack. This includes securing data in transit between monitoring agents, collection endpoints, and analysis platforms. The implementation of mTLS with Linkerd and EnRoute demonstrates how service mesh technologies can provide the cryptographic foundation required for FIPS compliance.
Automation plays a crucial role in maintaining continuous compliance. The IEEE analysis of FedRAMP's future direction emphasizes the importance of automated assessment capabilities and streamlined authorization processes. Organizations should implement automated compliance reporting, continuous security validation, and AI-driven anomaly detection to meet evolving federal requirements.
Integration with existing DevOps and SecOps workflows is essential for successful adoption. The convergence of DevOps and SecOps in Kubernetes environments requires observability solutions that can seamlessly integrate with CI/CD pipelines while maintaining security boundaries and compliance requirements. This includes implementing proper access controls, audit logging, and incident response workflows that align with federal standards.
Cost and Performance Analysis
The financial implications of implementing FIPS and FedRAMP observability are substantial but must be weighed against the requirements for federal compliance. According to Stack Armor's comprehensive cost analysis, initial FedRAMP compliance costs range from $500,000 to $1,000,000 for small to mid-sized cloud service providers, with ongoing annual maintenance costs adding another $200,000 to $500,000.
FIPS-validated observability tools introduce additional performance considerations due to stronger cryptographic operations. The Ping Identity analysis shows that servers running in FIPS-compliant mode may experience increased CPU usage and latency due to enhanced encryption requirements. However, modern implementations like Go's native FIPS 140-3 validated cryptographic module minimize overhead through optimized architectures.
Cost optimization strategies can significantly reduce operational expenses. The 2025 infrastructure monitoring buyer's guide indicates that techniques such as data sampling and AI-driven predictive operations can reduce data storage and processing costs by 60-80%. Organizations must balance security requirements with operational efficiency to achieve sustainable compliance.
The broader market context shows strong growth potential. The global observability tools and platforms market is projected to reach $34.1 billion in 2026, with federal spending on cloud services expected to exceed $30 billion by fiscal year 2028 according to TBR's federal cloud ecosystem report.
Federal Agency Adoption Trends and Drivers
The adoption of cloud-native observability solutions across federal agencies is accelerating, driven by digital transformation initiatives, enhanced security requirements, and operational efficiency mandates. Current indicators show that 55% of government cloud decision-makers have adopted distributed cloud-native databases, a key component of modern observability stacks.
The momentum continues to build, with cloud-native observability tools experiencing a 41% rise in adoption in 2025. This growth is particularly pronounced in federal environments where agencies must balance innovation with stringent security requirements and compliance mandates.
Key adoption drivers include compliance with federal mandates such as the Federal Cloud Computing Strategy (Cloud Smart), operational visibility requirements, cost efficiency pressures, and the need for enhanced security posture. The Forrester analysis of federal cloud security emphasizes the critical role of observability in maintaining security and compliance across distributed cloud environments.
Challenges remain significant, as highlighted in the GAO report on federal cloud adoption, including staffing constraints, technical complexity, and resource limitations. However, the evolution toward FedRAMP 20x initiatives aims to address these challenges through automation and streamlined processes, making compliant observability solutions more accessible to federal agencies.
Ready to implement FIPS and FedRAMP-compliant observability for your federal cloud environment? Contact Saaras to learn how our solutions can streamline your compliance journey while maintaining operational excellence.
FIPS-validated observability tools incorporate cryptographic modules that meet stringent federal security standards, ensuring data protection through validated encryption algorithms and key management processes. Unlike standard tools that may use flexible encryption approaches, FIPS solutions require certified cryptographic implementations. Organizations implementing these solutions should consider platforms that integrate seamlessly with existing infrastructure while maintaining compliance requirements.
FedRAMP-compliant observability implementation typically requires 12-24 months, depending on the organization's existing infrastructure and security posture. The process involves security control implementation, documentation preparation, third-party assessment, and agency authorization. Leveraging pre-authorized solutions and reusable security packages can significantly reduce implementation timelines while ensuring comprehensive compliance coverage.
Common implementation challenges include cost management, technical complexity, staffing constraints, and continuous monitoring requirements. Organizations often struggle with integrating FIPS-validated cryptographic modules while maintaining performance standards. Successful implementations require careful planning, automated compliance reporting, and comprehensive staff training to address these challenges effectively.
FIPS and FedRAMP compliance requirements can introduce performance overhead due to stronger cryptographic operations and comprehensive logging requirements. However, modern implementations minimize this impact through optimized architectures and efficient cryptographic modules. Organizations should evaluate solutions that balance security requirements with operational performance to maintain effective system monitoring capabilities.
Organizations implementing FedRAMP observability typically see ROI through reduced incident response times, improved security posture, and streamlined compliance processes. Studies show potential MTTR improvements of up to 80% with advanced observability tools. Additionally, pre-authorized solutions can reduce authorization costs and timelines, providing significant value for organizations serving federal markets while ensuring comprehensive security coverage.




.jpg)