What Actually is FIPS 140?
At its core, FIPS 140 is the U.S. government's benchmark for validating cryptographic modules. It ensures that the "lock" on your data isn't just strong in theory (like using AES-256), but is implemented with "chemically pure" correctness in the binary itself.
For SaaS leaders, understanding the security levels is critical:
- Level 1: The standard for software-only modules. It focuses on the logical correctness of the algorithms. This is the target for most cloud-native applications and Kubernetes components.
- Level 2-4: These require increasing degrees of physical security, such as tamper-evident seals or epoxy potting, typically reserved for Hardware Security Modules (HSMs).
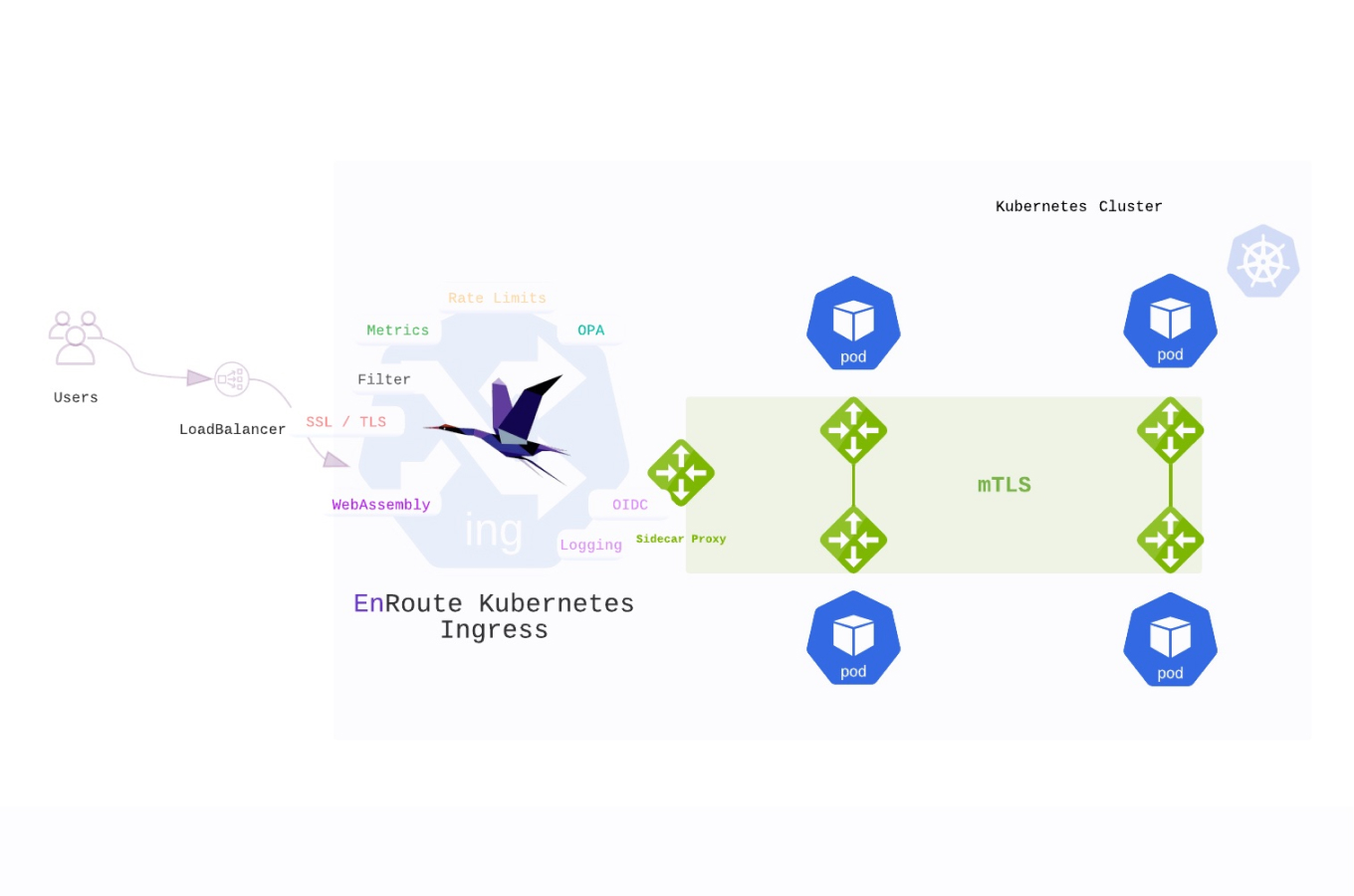
Compliance isn't limited to storage; it governs data in three states: at-rest (databases), in-transit (TLS/mTLS), and in-use. If your application transmits sensitive data, the SSL/TLS libraries handling that traffic must be FIPS-validated.
The Ticking Clock: FIPS 140-3
The landscape is currently shifting under the feet of DevOps teams. The industry is transitioning from the legacy FIPS 140-2 standard to the more rigorous FIPS 140-3.
- The Deadline: FIPS 140-2 modules move to the "Historical List" on September 21, 2026.
- The Risk: If you are building your federal strategy on 140-2 modules today, you are effectively building on an expired foundation. New federal procurements and ATOs (Authority to Operate) are increasingly prioritizing FIPS 140-3 readiness.
The Engineering Reality: Build vs. Buy
Achieving FIPS compliance in a modern stack-specifically with Istio and Envoy-is deceptively difficult. You cannot simply apt-get install a compliant proxy.
To build this in-house, your team must:
- Source the exact FIPS-validated source code (e.g., Google’s BoringCrypto).
- Compile it with specific, rigid build flags that match the NIST Security Policy perfectly.
- Maintain that build pipeline forever. If you patch a functional CVE but change the checksum of the crypto module, you invalidate your compliance.
One mistake in the linker flags renders your binary non-compliant, potentially costing you your FedRAMP certification.
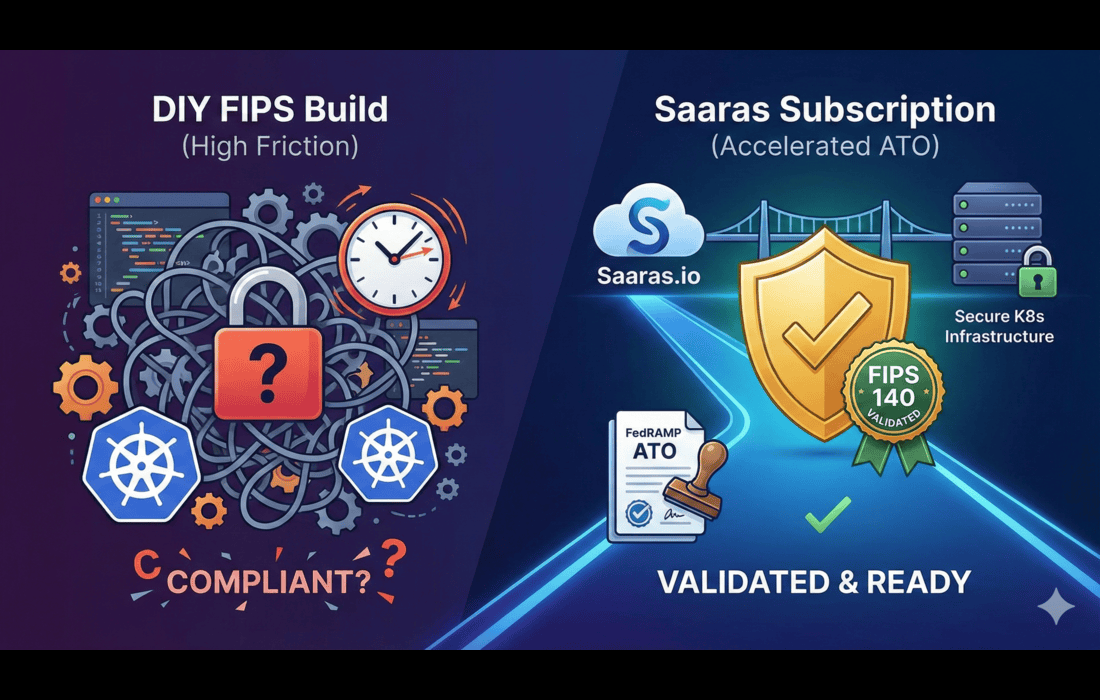
The Saaras Approach
This is why we built the Saaras Istio FIPS. We treat compliance as a managed infrastructure component, not a DIY project.
Instead of burning expensive engineering cycles on maintaining custom build pipelines, Saaras provides a drop-in subscription. We handle the rigorous validation against NIST standards and ensure you are ready for the FIPS 140-3 transition. This allows your team to inherit our validation, effectively by months.
With Saaras, your automatically enforce compliant mTLS, solving the "data-in-transit" requirement across your entire cluster.
For a CTO, the math is simple: Do you want your best engineers fighting with linker scripts, or shipping features?
Compliant" is a self-attestation; "Validated" is a formal NIST certification. Federal auditors require specific NIST Certificate Numbers for the modules. Without these active certificates, your FedRAMP application will likely be rejected.
FIPS 140-2 moves to the "Historical List," making it invalid for new procurements. Building on 140-2 today creates immediate technical debt. You should deploy FIPS 140-3 ready infrastructure now to avoid an emergency re-architecture later.
Building requires dedicated headcount to manage toolchains, CVEs, and potential lab fees ($50k+). Buying a subscription shifts this liability to the vendor
It introduces slight latency during TLS handshakes (RSA operations) but has negligible impact on throughput (AES-GCM). Using an optimized sidecar architecture ensures your application logic remains fast while the mesh handles the heavy cryptographic lifting.